Authentication payload
Once the APP receives the request confirmation (auth_wait and uuid), it should tell the user to start its PKSA to approve or reject the authentication request before the request expires.
The application must provide the user with out-of-band data. These data will be read by the PKSA in order to know which HAS server to connect to and to privately share an authentication key (auth_key) used to encrypt payloads.
This can be done by providing the user with a deep link or QR code representation of that deep link.
To create the deep link:
1. Create an auth_payload object:
auth_payload
{
account: string
uuid: string,
key: string,
host: string
}account: the username of the account performing the authentication.uuid: the request identifier received with theauth_waitreply.key: the app-generatedauth_key(see Encryption Key)host: URL of the HAS server the APP is connected to (ex: "wss://has.hiveauth.com")
2. Convert the auth_payload object to a base64 string (auth_payload_base64)
The URI for the deep link will be:
has://auth_req/{{auth_payload_base64}}
Example:
The following auth_payload
will generate the following URI:
has://auth_req/eyJhY2NvdW50IjoiYXJjYW5nZSIsInV1aWQiOiI5YjBlMmRjMy1mNTc0LTQ3NjYtYWJkZC1jNDI5ZGNlMTEyODQiLCJrZXkiOiIwM2Y2MzQ2OS01YTM1LTQ3Y2ItYTZiNC1lOGM0ZDMxNDRjZjkiLCJob3N0Ijoid3NzOi8vaGFzLmhpdmVhdXRoLmNvbSJ9
and will produce the following QR code
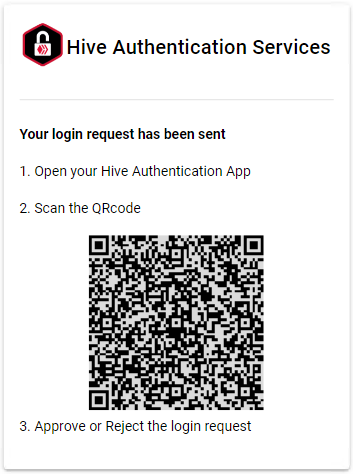
Last updated